Recently the North American Electric Reliability Corporation, working in tandem with the Electricity Information Sharing and Analysis Center, released its summary of Lessons Learned from its fifth biennial electrical power grid and emergency response exercise, GridEx V.
 An Ounce of Prevention: The Power of Deliberate Planning
An Ounce of Prevention: The Power of Deliberate Planning

Greg Pollmann, Principal Industrial Consultant | Dragos
Recently the North American Electric Reliability Corporation (NERC), working in tandem with the Electricity Information Sharing and Analysis Center (E-ISAC), released its summary of Lessons Learned from its fifth biennial electrical power grid and emergency response exercise, GridEx V. The release of this report prompts a discussion about the perspectives of deliberate incident response planning and some of the common pitfalls the Dragos Professional Services team has seen during customer exercises throughout 2019, such as: preparing for the unexpected, establishing an emergency response plan, declaring incident thresholds, keeping up-to-date playbooks, and assessing the effectiveness of cross-functional communication.
In the report, NERC recommends organizations identify and plan for impacts to key components of critical systems well before a cyber incident occurs; that organizations should establish planning cadence and cycles to allow purposely built flexibility and coordination of response actions; and that organizations should concentrate on crisis communication tools and their integration into response and recovery actions. Likewise, in the 2019 Year In Review, Dragos discloses similar observations made during facilitations of tabletop exercises and planning improvement workshops. Taken together, these observations seem to show a trend that directly correlates to the amount of rigor applied to deliberate planning. Both reports agree that cyber incident response planning should tie the continued knowledge gain of consequence, threat intelligence, and vulnerability analysis to the planning of actions and resource employment necessary for effective response and recovery. Additionally both reports imply that organizations should not compound the impact of these attacks by simply reacting to them from an unprepared state. Organizations should deliberately plan incident response and recovery actions methodically to minimize the cascade of impacts to both bottom line operations and consumers.

From Dragos’ 2019 ICS Year in Review report: Lessons Learned from the Front Lines, 67% of Tabletop Exercises required additional preparation. In multiple instances, the incident response plan (IRP) was not known or referenced by the analysts responsible for performing the response.
To buck the trend and ensure your team isn’t caught flat footed during an incident, it may be time to dust off your Cybersecurity Incident Response Plan and go to work. Here are some easy wins to implement in your effort.
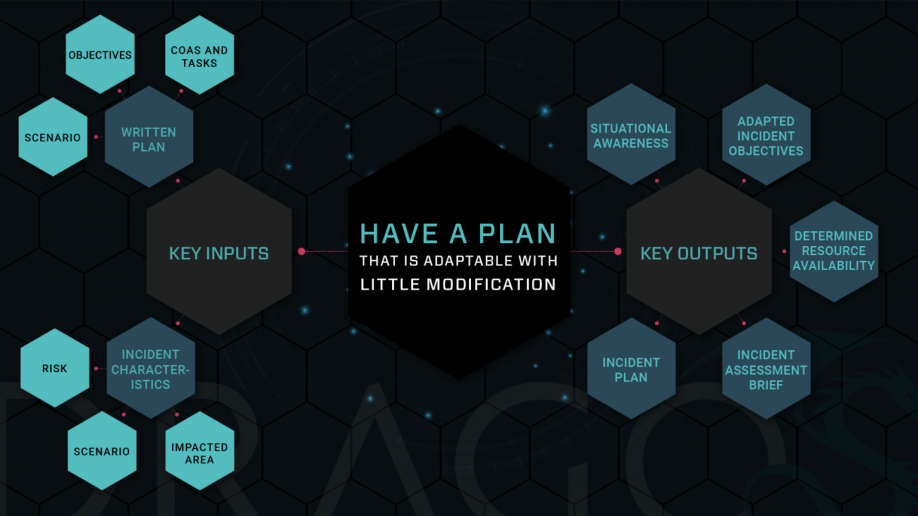
Planning for the most likely, or most dangerous, scenario means you will be better prepared to respond to the unexpected. Many businesses and organizations jump right into action when they are directly confronted with a crisis, or in this case, a cyber incident. They meet the situation head on with whatever or whomever they have to resolve the incident and return to normal operations. After the incident is over, businesses often compile their lessons learned, lick their wounds, and the actions that were taken become a blueprint for incident response plans. We can learn invaluable lessons from reacting to an incident, but ultimately it is a “bad” way to plan. For starters, there is a marked distinction between reacting and responding. “Reacting” invokes quick action as a result of something that is unplanned and unforeseen. It involves tense and aggressive movements and typically provokes chain reactions that perpetuate the situation. This is not the way to blueprint planning. On the other hand, a deliberate response is completely different. It is proactive, the actions associated with it are thought out, calm, and don’t compound effects. Deliberately planning how you will respond to a cyber attack means that the risk scenarios have been studied, discussed, anticipated, and prepared for, and affected critical assets have been inventoried and their dependency has been accounted for. The goal of deliberate planning is to produce a plan that can account for the most likely, or most dangerous, scenarios and be adapted to any unforeseen crisis with little modification. Stated another way, a well thought out incident response plan can guide response and recovery activities and decision making even when unplanned incidents occur. At the very least, by taking this approach organizations identify the most critical logical functions, network services, and control assets that support their operational environment and bottom-line.
Example of FEMA Crisis Action Planning Model
Cyber Incident Response isn’t that different from other emergency response plans. Most industrial organizations can increase the effectiveness of their cyber incident response plans by integrating the common framework of existing emergency response plans. Often industrial organizations ask themselves, “What happens if I get hit with a cyber attack in my operating environment?” This is an extremely hard question to answer or plan for. You can’t determine the likelihood of a cyber attack and no one chooses to become the target of a cyber attack. But you probably understand the physical consequences of a cyber attack better than you think. In fact you probably already have a plan for the impact to operational assets, you just call it something else. An emergency response plan. The fallout of a cyber attack is oftentimes similar to those risks that are accounted for in other emergency response plans for natural disasters, fires, or equipment malfunctions. Additionally, coordinating your cyber incident response plan with existing emergency response plans ensures you avoid mission segmentation that often leads to cybersecurity and incident response fragmentation. This often results in cumbersome plan activations and mis-matched capabilities and resources. Most emergency response plans, at their core, share a common risk assessment and command, control, and communication structure. Use these common planning traits as building blocks to coordinate and correlate frameworks into your cyber incident response planning. Doing this will prove invaluable for intimately understanding your organization’s common response procedures and frameworks and will lead to unity of purpose if a cyber incident occurs. As we make headway across the industry, coordinating mission space to eliminate segregation, we should take care to also roll out the seams in coordinating response planning as well.
Declaring incident thresholds and updating response playbooks can give your responders a head start in response if an incident occurs. Triaging and analyzing cybersecurity events and their artifacts is generally regarded as the first step of incident recognition. But the thresholds for declaring an incident depend on factors such as recognizing threat behaviors and tactics, operational impacts to bottom line operations, and assumed risk. Identify the factors that contribute to your cyber risk thresholds and clearly define or update them to match your organizations defense / response posture. Time and time again incident declaration thresholds, defined within response plans, are not in lock-step with current operational risk assessments or current cyber threat intelligence; sometimes they don’t even exist. Organizations must learn to derive cyber incident declaration thresholds from cyber threat intelligence and assessments and incorporate this information into current incident response plans. This will eliminate knee-jerk or lethargic declarations and increase speed, proficiency, and recognition of events as discovered or detected. Additionally, pairing thresholds with response playbooks will facilitate more efficient and effective response procedures. Playbooks can provide a full context of actions and notifications. Plans and playbooks should be updated regularly to ensure security teams are versed in incident response best practices and have access to the most useful and relevant information associated with threats. Most critical infrastructure organizations do this now in the context of planning for naturally occurring hazards such as extreme weather events. Operations, Engineering and Emergency Management personnel know how their systems can operate in diminished capacity during periods of extreme wet weather, cold, high winds, etc. They may not be called “Playbooks” per se, but well functioning organizations have checklists and readiness procedures in preparation for these events, as well as, on staff expertise capable of maintaining operations in adverse conditions. The same amount of planning rigor should be applied to cybersecurity.
Effective communication is a game changer for employing resources and recognizing constraints while responding to an incident. Should a cyber incident be declared, the need to respond appropriately is immediate, followed by the need to communicate. An organization must know its stakeholders and responders and how to notify and communicate with them in advance of ever needing to do so during an incident.
Note: NERC recognizes and advises that crisis communications be incorporated into the integral parts of response planning at all levels. As a result, NERC encourages individual planners to include their organization’s crisis communications staff, as detailed in the GridEx V Exercise and Lessons Learned report.
Most organizations have not adopted a dedicated communications annex or framework within their existing cyber incident response plan. Having a comprehensive communications plan, consisting of policies, notification procedures, and incident command structure, ensures that a primary response management and employment mechanism is accessible during a cyber incident. A communications plan acts as a guide to help quickly activate, assemble, and employ resources and capabilities, informs the right stakeholders of resource requirements and constraints, and helps to guide and convey leadership or incident commander directives and objectives.
Conclusion
The concept of deliberate incident response planning is especially important for organizations that provide and operate critical infrastructure. Functioning critical infrastructure is the lifeblood of communities, societies, and civilization as a whole.
Industrial organizations must be prepared, and their staff empowered to deal with cyber incidents as they happen. Tomorrow’s cyber incident response teams must focus on building collaborative planning environments within their organizations that concentrate on accounting for what they are responsible for and coordinating with existing emergency response frameworks to add effectiveness, speed, and agility to their cyber incident response plans. Additionally, planning reviews and revisions need to include up-to-date operational risk and threat analysis to allow incident thresholds and playbooks to be created or updated. Preparation does not, and cannot, mean planning for every possible contingency. Preparation should focus on planning for those risks that are most likely to affect an organization while remaining adaptable to respond to the unexpected effectively. Lastly, irrespective of incident intensity, any incident response team must communicate in a mode and medium that is appropriate to the situation. Having a dedicated communication plan to leverage during an incident ensures that response teams maintain an appropriate level of communication for the duration of the incident, as well as after; ensuring transparency and consistent command of resources are applied throughout response and recovery. These recommendations will enhance the effectiveness of the type of planning required to meet the current threats faced today.
The content & opinions in this article are the author’s and do not necessarily represent the views of AltEnergyMag
Comments (0)
This post does not have any comments. Be the first to leave a comment below.
Featured Product

